
Crypto Safe Storage
It is very important to safely store crypto coins such as Bitcoin, because if the private key is lost or stolen, there is no possibility to reclaim the coins. The security aspect is divided into two parts: The secure storage of the private key and – in case of more professional storage – to make access to those keys independent of a single person or organization.
Schematic representation of cold storage facilities
Safely storing private keys
The starting point for the Crypto Index Fund is that a private key is by definition never exposed to any network whatsoever. To this end, all keys that give access to the crypto currencies are placed in so-called cold storage, where they are inaccessible to hackers.
One of the features of blockchain technology is offline transaction signing. With this form of signing, a transaction is encrypted with the private key on an airgapped (networkless) system. The encrypted transaction, from which the private key cannot be distilled, is used online to actually execute the transaction on the blockchain. When trading for our fund, we use this method to transfer the cryptocurrency to online trading platforms.
Although the storage of private keys can be easily secured against hackers, there are also physical threats; data carriers and private keys can be stolen. To prevent this, it is important to keep the media on which the private keys are stored in a secure location. To this end, the fund uses highly secure locations that meet the most stringent security requirements.
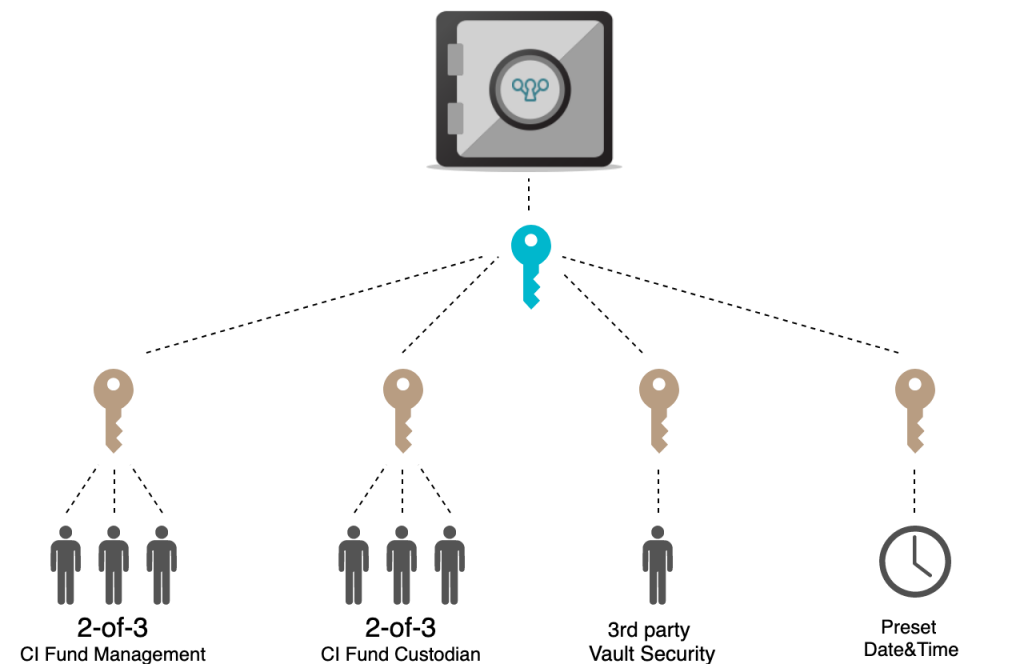
Storage independent of individual persons and organisations
For an individual person, the above method of security may be sufficient. Nevertheless, there remains a vulnerability: persons who have formal access to these locations can abuse their rights, whether or not they are forced to do so. An additional layer of security is therefore needed, which makes it impossible for an individual person – and even for a single organisation – to gain access without other parties.
The Crypto Index Fund applies extensive procedures to ensure the safekeeping of crypto. Access to locations is procedurally secure: there will always be a known number of people (no more and no less) from different organizations present and everyone has to identify oneself in order to gain access. Furthermore, the physical and digital access to the media on which the private keys are stored is protected with multisig technology, so that the passwords of several parties are needed to make the keys available (see picture on top).

